Hardware Bypass Firewall . A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. The cisco firepower 4100 series security appliance is a standalone modular security services platform. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. Nmap implements many techniques for. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. It is capable of running multiple security. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a.
from www.linkedin.com
while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. Nmap implements many techniques for. The cisco firepower 4100 series security appliance is a standalone modular security services platform. It is capable of running multiple security. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure.
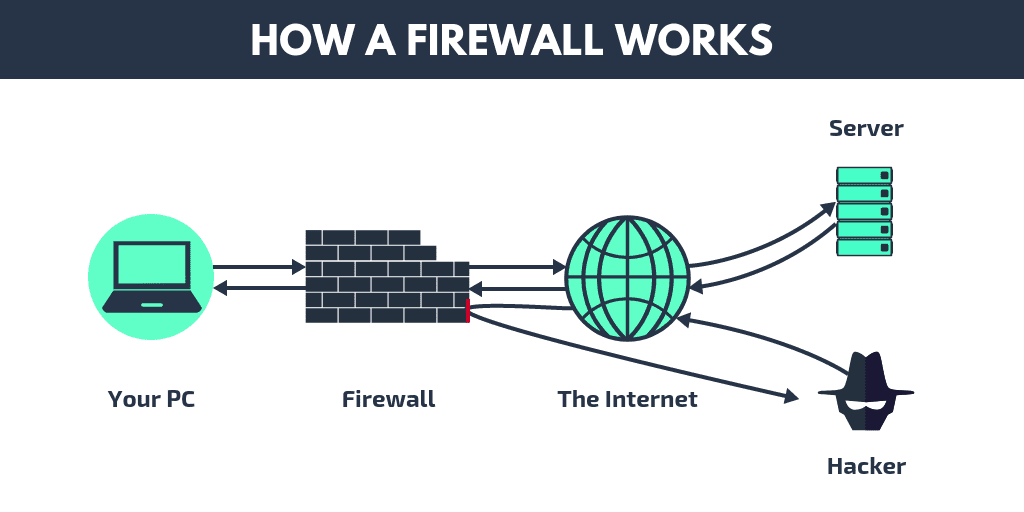
How does a Firewall work
Hardware Bypass Firewall Nmap implements many techniques for. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. Nmap implements many techniques for. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. It is capable of running multiple security. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. The cisco firepower 4100 series security appliance is a standalone modular security services platform. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal.
From kratikal.com
"Top 5 ways hackers can bypass your firewall” Kratikal Blogs Hardware Bypass Firewall A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. Nmap implements many. Hardware Bypass Firewall.
From www.youtube.com
Free software to bypass firewall/opendns YouTube Hardware Bypass Firewall Nmap implements many techniques for. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with. Hardware Bypass Firewall.
From www.youtube.com
9 Nmap Decoy Scan Bypass Firewalls What Is Firewall Bypassing Hardware Bypass Firewall It is capable of running multiple security. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. Nmap implements many techniques for. The cisco firepower 4100 series security appliance is. Hardware Bypass Firewall.
From kratikal.com
ByPass Application Firewalls Kratikal Blogs Hardware Bypass Firewall The cisco firepower 4100 series security appliance is a standalone modular security services platform. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. hardware bypass pair—a pair of ports or ethernet interfaces that can. Hardware Bypass Firewall.
From www.alibaba.com
R673bg 1u Firewall Hardware Server 6* Lan Bypass Firewall Appliance Hardware Bypass Firewall It is capable of running multiple security. The cisco firepower 4100 series security appliance is a standalone modular security services platform. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. Nmap implements many techniques for. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap.. Hardware Bypass Firewall.
From www.guidingtech.com
6 Ways to Disable Firewall on Windows Guiding Tech Hardware Bypass Firewall The cisco firepower 4100 series security appliance is a standalone modular security services platform. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. in this post on firewall solutions, we focus on the. Hardware Bypass Firewall.
From freepctech.com
6 Simple Ways to Bypass Firewall Free PC Tech Hardware Bypass Firewall while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. It is capable of running multiple security. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap.. Hardware Bypass Firewall.
From www.linkedin.com
How does a Firewall work Hardware Bypass Firewall while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. The cisco firepower 4100 series security appliance is a standalone modular security services platform. A virtual private network (vpn) can help bypass firewalls and intrusion detection. Hardware Bypass Firewall.
From www.guidingtech.com
6 Ways to Disable Firewall on Windows Guiding Tech Hardware Bypass Firewall in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. Nmap implements many techniques. Hardware Bypass Firewall.
From www.allfirewalls.de
FortiGate 80FBypass Firewall (FG80FBYPASS) Günstig kaufen Hardware Bypass Firewall It is capable of running multiple security. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. The cisco firepower 4100 series security appliance is a standalone modular security services platform. Nmap implements many techniques for. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a. Hardware Bypass Firewall.
From medium.com
Bypass Windows Firewall using Nmap Evasion Techniques WiktorDerda Hardware Bypass Firewall hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. It is capable of running multiple security. Nmap implements many techniques for. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. The cisco firepower 4100 series security appliance is a standalone. Hardware Bypass Firewall.
From bachelor-tech.com
Disabling default Proxmox firewall Bachelor Tech Hardware Bypass Firewall The cisco firepower 4100 series security appliance is a standalone modular security services platform. in this post on firewall solutions, we focus on the top firewall bypassing techniques with tools nmap. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. hardware bypass pair—a pair of ports or ethernet. Hardware Bypass Firewall.
From hackingnewideas.blogspot.com
Hacking with new ideas Hardware Bypass Firewall hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. It is capable of running multiple security. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing. Hardware Bypass Firewall.
From tech4gamers.com
How To Disable Firewall? [All Methods Guide] Tech4Gamers Hardware Bypass Firewall hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. The cisco firepower 4100 series security appliance is a standalone modular security services platform. It is capable of running multiple security. Nmap. Hardware Bypass Firewall.
From dev.to
Seamlessly Bypass Firewalls With The AllNew CustomHeaders Capability Hardware Bypass Firewall A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. The cisco firepower 4100 series security appliance is a standalone modular security services platform. Nmap implements many techniques for. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a.. Hardware Bypass Firewall.
From www.wikihow.com
9 Easy Ways to Bypass a Firewall or Filter Hardware Bypass Firewall hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. The cisco firepower 4100 series security appliance is a standalone modular security services platform. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure. in this post on. Hardware Bypass Firewall.
From worldwideprogramers.blogspot.com
Tutorial Bypassing Firewall on a Server Hardware Bypass Firewall hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. Nmap implements many techniques for. It is capable of running multiple security. while mapping out firewall rules can be valuable, bypassing rules is often the primary goal. The cisco firepower 4100 series security appliance is a standalone. Hardware Bypass Firewall.
From www.youtube.com
bypass firewall using ssh tunneling YouTube Hardware Bypass Firewall The cisco firepower 4100 series security appliance is a standalone modular security services platform. hardware bypass pair—a pair of ports or ethernet interfaces that can be associated with each other with underlying support for a. Nmap implements many techniques for. A virtual private network (vpn) can help bypass firewalls and intrusion detection systems by routing traffic through a secure.. Hardware Bypass Firewall.